If Jim Browning Can Get Tricked by A Phish, Anyone Can!
For years, I’ve watched and enjoyed Jim Browning scam-baiting and exposing scammers on YouTube. In one nerve-racking episode, Jim collaborated with fellow YouTuber Karl Rock to try and shut down scammers’ call centers in India.

Unfortunately, Jim Browning has just lost his YouTube channel, which had over 3.3 million subscribers. Jim has admitted that it was a result of a scam. Yes, the master of scam exposure fell for the very scams that he works so hard to scuttle! Jim himself has admitted that anyone can fall for a scam regardless of how tech-savvy they might be.
On July 27 Nicola Selenu, a noted deliverability and anti-abuse consultant, published some details about how it all happened at https://www.linkedin.com/pulse/someone-just-scammed-jim-browing-tricking-him-deleting-nicola-selenu/ using information that Jim apparently, and generously, provided. Sure enough, it was just a well-crafted phishing attack.
Jim has largely been dealing with scam call centers, the majority of which are in India. The scammers send phishing emails, call, and shove pop-ups on the computer screens of their unsuspecting victims. The victims then feel compelled to get in touch with the scammers, typically with a resulting loss of their money.
Senior citizens, who are often not very tech-savvy, are a frequent target of these schemes. The payoff portion of the scams take many forms, but they all start with social engineering. No need for sophisticated or brute force hacking of the victim’s computer or accounts is needed if the perpetrator can come across as genuine.

A lot of people would find it surprising that Jim, who’s totally immersed into fighting scammers, would fall for a scam himself. But think about it: how are we supposed to judge genuineness? When faced with social engineering, what evidence do we have to go on when it comes to judging genuineness.
The people I work with use the metaphor of an office building receptionist to illustrate the fact that we simply do not have accountability methods that have been used in the physical world for centuries.
Think about that office building lobby receptionist for a moment. Do we tell them to determine the intentions and character of every person walking through the door? Of course not! Instead, we instruct them to get some ID, establishing who is accountable for what happens while the visitor is in the building.
So where are the digital IDs of measurable reliability?
The internet used to be called the information highway, and the name still fits. So what is a highway but an outdoor public transport system? You don’t need an ID to be in most outdoor spaces, but you tend to know who’s in a room with you in an indoor space. Buildings are more than protection from the weather: they are places of accountability. And accountability starts with knowing the identities of the people in them.
Imagine managing YouTube accounts by walking up to an outdoor billboard or a roadside stand. The assumption is that whatever part of your YouTube account you’re trying to manage, the person you’re talking to is who they claim to be, with absolutely no supporting evidence.
We’re not only managing our YouTube accounts on an outdoor billboard, we’re doing our banking on an outdoor billboard. Whose idea was that?!
Well, this isn’t going to be transformed overnight, is it? We need a measurably reliable source of identity in online spaces, and in the meantime, we are as vulnerable as a homeless person working, living, and letting their kids hang out in a cardboard box beside the information highway.
See, the problem isn’t with the highway. The internet highway does its job well, moving bit packet vehicles around the world with incredible efficiency. It’s a marvelous outdoor transport facility.
It’s just… where are the secure indoor spaces? The buildings? The internet isn’t failing us, we’re just using it the wrong way. We’re living and working on the side of this busy information highway. Those of us who understand that we are using the internet wrongly are not the least bit surprised by the resulting mayhem. What did we expect?
How are we using the internet wrongly? The information security problem is about inauthenticity and the lack of accountability. The root cause of the problem is simply the fact that anyone can masquerade as someone else on the internet. If we don’t deal with that, no level of user education or security technology is going to save us.
Under ideal circumstances, even the best security technologists will fall for a scam. The moment you interact with that initial email or pop-up message, you are halfway deep into the scam. Who can truthfully claim that they can trust all the messages and calls they receive? Absolutely nobody!
There’s a good chance the loss of Jim Browning’s YouTube channel started with a seemingly harmless message. He’s promised to tell the whole story later. I’ve placed my bet on it being a social engineering scam.
So, what is the solution?
The solution is being able to reliably weigh the trustworthiness of any message or call that we receive on our devices by having a reliable way to hold the sender accountable.
Does that mean leaving our identity information with everything we do on the Net?
Let’s look to another very old method for the answer: the license plate. Anyone can see your car’s license plate, but no one gets to know the identity of the driver unless there’s been an incident.
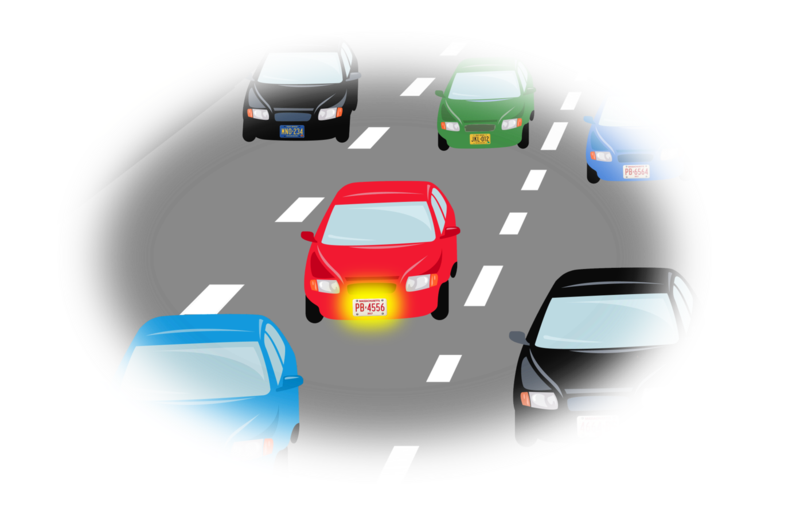
Then it’s up to the operator of the destination space – the indoor space – to specify what they need to know about the visitor. Simple accountability should be sufficient in most cases: that is, if they do something injurious or illegal there is a way for the injured party to uncover their identity.
There should be a path to identifying miscreants and holding them accountable.
PKIDR (PKI Done Right) will help us implement measurably reliable digital signatures everywhere. The signatures will be backed by digital certificates that are owned and tied to real people. A measurably reliable digital signature will help you gauge whether you can trust the source of a message. It will provide the trust anchor we need.
Watch this three-part video to learn what is PKI & PKIDR and how they can help us bring social engineering to an end once and for all.
